
Palo Alto Networks discloses RCE zero-day vulnerability
Threat actors have exploited the remote code injection flaw, which affects the GlobalProtect gateway in Palo Alto Networks' PAN-OS software, in a 'limited' number of attacks.
A critical zero-day vulnerability in Palo Alto Networks' PAN-OS software is under active exploitation.
Palo Alto Networks published a security advisory Friday detailing a command injection flaw, tracked as CVE-2024-3400, in the GlobalProtect gateway feature of the vendor's PAN-OS software for next-generation firewalls. The zero-day vulnerability affects specific versions of the OS and "distinct feature configurations may enable an unauthenticated attacker to execute arbitrary code with root privileges on the firewall," the company said.
"Palo Alto Networks is aware of a limited number of attacks that leverage the exploitation of this vulnerability," the advisory said.
The remote code injection (RCE) vulnerability, which was discovered by cybersecurity vendor Volexity, received a CVSS score of 10.
In a post on X, formerly known as Twitter, Volexity President Steven Adair said his company "caught a threat actor using an unauthenticated RCE in Palo Alto Networks GlobalProtect." In a follow-up post, he said multiple customers had been affected.
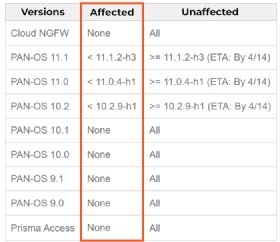
Palo Alto Networks said CVE-2024-3400 affects specific versions of PAN-OS 10.2, PAN-OS 11.0 and PAN-OS 11.1 in firewalls that have both GlobalProtect gateway and device telemetry features enabled. The company said it expects to deploy patches by April 14.
In the meantime, Palo Alto Networks recommended temporary mitigations. Customers with Threat Prevention subscriptions should enable "Threat ID 95187" to block exploitation of the zero-day vulnerability. Customers without subscriptions should temporarily disable the device telemetry feature until their firewalls have been patched.
Palo Alto Networks said customers can check for signs of compromise by opening a case in the vendor's customer support portal and uploading technical support files to determine if log data matches known indicators of compromise for the zero-day.
Rob Wright is a longtime reporter and senior news director for TechTarget Editorial's security team. He drives breaking infosec news and trends coverage. Have a tip? Email him.






