operational-level agreement (OLA)
What is an operational-level agreement?
An operational-level agreement (OLA) is a contract that defines how various IT groups within a company plan to deliver a service or set of services. These agreements are designed to address and solve the problem of IT silos. They set out specific criteria and define the IT services for which each department is responsible.
Departments or business functions within an organization execute OLAs. For example, IT departments might execute them for specific functions, such as networking or security services. They describe how each service is to be performed and delivered.
OLAs are different from service-level agreements (SLAs), which are contracts and agreements between vendors and their customers. OLA's are commitments within an organization. They are just as important as SLAs, however, because they define what's required to meet the internal customer's approval and what happens when those needs aren't met.
Like SLAs, OLAs are important business tools and should be executed for all major projects as well as smaller, less consequential initiatives.
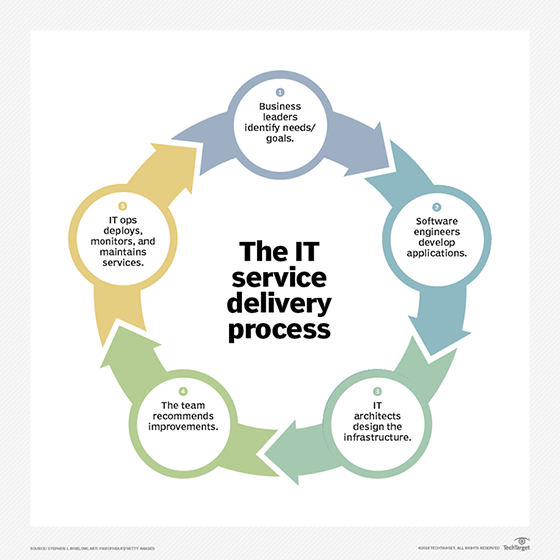
Why are OLAs important?
The most important reason for having OLAs is to ensure that what has been agreed to -- such as the delivery schedule for a service or product -- is what happens. OLAs are also important as a way to define what happens if the product or service isn't delivered to internal customers in the agreed time frame, and what recourse the customer has. Both are key elements in IT service-level management, ensuring that superior performance is delivered.
OLAs can include some or all of the following metrics:
- Key performance indicators.
- Qualifications of people performing the work.
- Delivery dates.
- Incident management.
- Response times.
- Criteria for escalation.
- Installation dates.
- Mean time between failures.
- Mean time to repair.
These criteria are used to compare performance in the context of the metrics and to determine if the OLA has been satisfied.
Who uses OLAs?
OLAs are typically used in IT environments as part of the IT service catalog. This is because many IT activities have performance components associated with them. Other departments might also execute OLAs to provide details of an internal service they perform for another part of the organization. For example, a production department might ask the finance department to prepare an analysis of the return on investment of a production system.
OLAs are often agreed upon with a handshake. Nevertheless, these agreements provide details and expectations of the activity in question. As a result, they reduce the likelihood of misunderstandings.
Preparing an OLA
IT organizations should establish a standard process and template for preparing OLAs that includes the following steps:
- Provide a general overview that states the OLA's purpose and scope.
- Define the issues the OLA is to address.
- Specify the product or service to be provided.
- Identify the stakeholders involved with their contact information.
- Describe the scope of work and desired results.
- Determine the desired time frame, any intermediate phases and goals, and the end date.
- Outline how and how frequently the parties involved will communicate.
- State any specific terms of service or other conditions required.
- Include additional information and relevant content such as diagrams and lists, as attachments.
- Have interested parties sign the agreement, authorizing the work.
What is a service-level agreement?
The term service-level agreement is used in many organizations to refer to agreements between internal groups. However, according to the Information Technology Infrastructure Library (ITIL) framework for best practices, this type of internal contract should be called an operational-level agreement. SLAs are more often executed between an organization and one or more of the vendors that the organization does business with.
An SLA describes what products or services the vendor is to provide, the criteria under which the products and services are to be provided, and what happens if the product or service provider fails to perform as stated in the SLA. These situations may include failure to meet the product or service delivery date, penalties if the service fails once it's installed and other situations that violate the SLA terms. Penalties for failing to meet a service agreement might include a credit or a refund for the product or service provided or a discount on a previously agreed to price or rate.
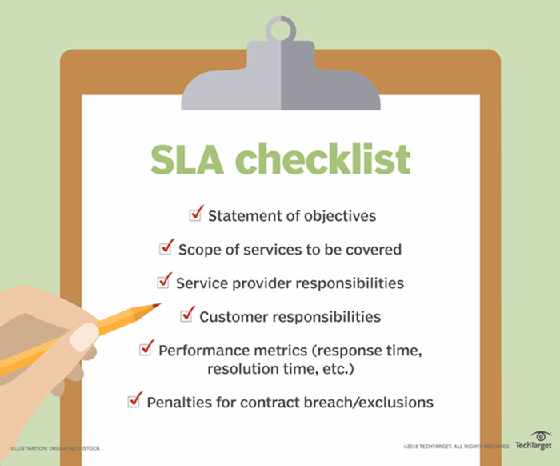
Relationship between OLAs and SLAs
OLAs can be implemented on their own. However, they are also used to delineate the specific activities and relationships needed to achieve the specifications in a related SLA. Figure 1 depicts the typical relationships between OLAs and SLAs.
SLAs interact with OLAs; typically, the OLA specifies the tasks and activities that must be delivered, such as networking and security, to meet an underpinning contract that's part of an SLA. Criteria specified in the OLA is embedded in the SLA, which is executed with a vendor.
Learn more about ITIL best practices and how they improve business processes.
